02 May, 2023

Many organizations are rapidly adopting, migrating, or expanding their use of the cloud. In some cases, teams need the ease of data access, others want the convenience of cloud-enabled SaaS applications, in addition to a multitude of other reasons. The value, availability, and scalability of the cloud are too significant to ignore, but the risks, complexities, and variables are as well.
When selecting a cloud model for your organization, it is important to keep in mind that one size does not fit all. A recent survey (1), found that 49% of IT decision-makers globally see cybersecurity risks around cloud adoption as being considerably threatening to their business – and in the UAE, this number stands at 58%. The reasons behind these concerns are broad, spanning numerous areas, and many are vital reasons for cloud migrations failing, such as lack of planning, selecting the wrong migration approach, going too big too soon, not testing thoroughly, and overlooking the human element.
In fact, 74% of IT decision-makers surveyed (2) moved an application back from the cloud to their internal on-premises infrastructure due to performance or security issues. This can have a significant impact resulting in disruption of critical and essential services, considerable cost variance and project delays, and most importantly, lessen stakeholder confidence and support.
Moving on the cloud migration journey, ensure critical decisions have been reviewed and agreed upon at an organizational level—considerations around cloud strategy, cloud policy, data classification, handling policy and guidelines, and more. The adoption of a cloud application must be evaluated and justified for the business, IT, and operations.
It is mandatory that a security assessment is conducted throughout each project phase, from initiation, design, implementation, post-production, through support and maintenance. The assessment criteria differ depending on the stage of the project. Moreover, the assessment is a shared activity and is conducted with the help of responses received from business leaders, operations, IT, and the cloud service provider.
At the initiation phase, an evaluation is conducted to look within the organization and understand if there is indeed a need for cloud. The enterprise information assets to be processed and stored by the cloud must be identified and evaluated to determine asset classification and criticality. Business processes must also be assessed to understand their criticality and availability requirements.
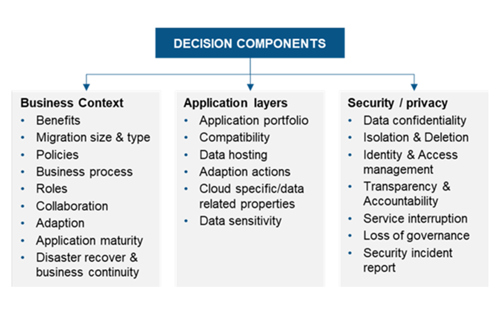
Several aspects are considered at this stage, such as:
This is where a key decision is evaluated and it is determined whether a specific business process can be migrated to cloud versus left and maintained on internal infrastructure. When a process is migrated, a decision on the level of control must be made, specifying the aspects to be left in-house.
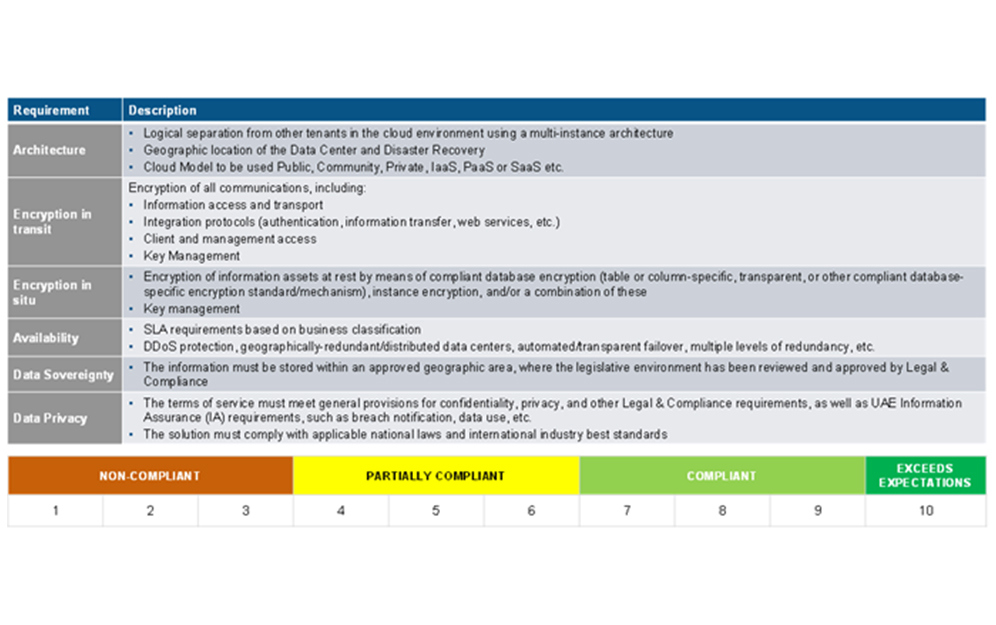
The following provide a basic level of control guidance:
The evaluation is based on responses received for components within a business context, application layers and security/privacy context (as shown below).
In this phase, the cloud service provider and the proposed cloud application are evaluated against the essential security compliance requirements of the organization. Criteria like the objective of the assessment, the decision framework, and UAE and industry best cybersecurity requirements will be analyzed.
A useful analysis technique in this phase is the development of organization-specific impact criteria. Impact criteria should, at a minimum, include financial (fines and legal penalties), productivity, business availability, tangible losses, physical security, and reputational loss.
Risk mitigation – reduction, acceptance, or transfer – will also be dependent on the organizational risk tolerance threshold.
This step in the risk management process often requires further analysis of the risk factors to establish a practical course of action or cost-justification for a plan of remediation. Upon completion, the residual risk must be presented to management, including risk owners, so a decision for cloud adoption can be made.
Security is a shared responsibility among all facets of an organization. A critical success factor for the assessment process is ensuring all stakeholders, including business, IT, security, and cloud service provider are part of the assessment and the eventual findings and remediation.
Security must be addressed from the beginning of the project and continue to be evaluated throughout, even after its completion. This will ensure the organization proactively manages its network and cloud environments, rather than putting out fires as they arise after deploying new technologies.
1. Equinix 2022 Global Tech Trends Survey
2. Fortinet and IHS Markit, The Bi-Directional Cloud Highway
Author:Shivani Jariwala
Caption - Many organizations are rapidly adopting, migrating, or expanding their use of the hashtag#cloud.When selecting a cloud model, it is important to keep in mind that one size does not fit all. In this article, we explain how your organization can proactively manage its hashtag#network and cloud environments.